Nikola Sever
PRINCIPAL CONSULTANT
A company can buy the best and most expensive devices to increase their security level, train their employees to safely store either their own or the company’s secrets, implement the most sophisticated video surveillance system, and yet, still remain completely vulnerable. Security – in this case IT security – is often just an illusion. One which is created through a false sense of security that is based on the fact that the company is relying on hardware firewalls, cutting-edge antivirus software, automatic updates, policies banning the use of removable storage devices or restricting internet access to certain websites, etc.
Those who believe in creating a “secure” environment by only using security systems, devices and/or apps are simply fostering the illusion of being secure. As the renowned security expert Bruce Schneier says: “Security is a process, not a product.” Even more than that, security is not a technical issue, but an issue that concerns people and management.
Just think about how many times we, as children, were manipulated by the great social engineering experts – namely, our own parents. Every time, they would find a way to make us do things “for our own good,” things that they believed were the best for us at that particular moment. Parents, by necessity, become manipulators just as social engineers manipulate unfortunate individuals/groups into doing things they are not even aware that they are doing.
What is social engineering?
Social engineering is the term used for a broad range of activities used to exploit human error or purpose to gain access to either information or services. It relies on different forms of manipulation to trick the victims into making a mistake or surrendering sensitive information. When it comes to cybersecurity, social engineering tricks users into opening documents, files, or emails, visiting websites, or providing malicious people with unauthorized access to services and systems. Even though such tricks can abuse technological failures, most often they rely on the human element to be successful.
Methods of social engineering
- Phishing: The main purpose is to steal sensitive information usually to obtain financial benefit
- Spear-phishing: same as phishing but the main targets are specific individuals
- Whailing: This is actually a type of spear-phishing, but here the main targets are people in high positions, for example: polititians, presidents, and C level executives.
- Smishing: Type of phishing conducted through SMS services
- Vishing: Type of phishing conducted through phone calls
- Business e-mail compromise: is a sophisticated scam, targeting businesses and organizations, where criminals employ social engineering techniques to gain access to an employee’s or executive’s e-mail account to initate bank transfers under fraudulent conditions
- Impersonation: when one entity illegitimately assumes the identity of another in order to benefit from it
Consequently, it is self-evident why this particular method is one of the most prevalent ones. Its biggest advantage is the fact that a relatively small effort can bring abou significant potential gains. To get ransomware, or malware in general, someone has to infect you with it, on purpose- it doesn’t appear from thin air.
Why is it so successful?
By continuously improving security technologies and reducing attack vectors, programmers are making it harder for malicious attackers to exploit their attacks, which is why these attackers are turning to exploiting the human element. This is possible, not because people are stupid or because they lack common sense, but because as humans, we are vulnerable to having our trust manipulated and exploited in some way. A social engineer anticipates suspicion and resistance, and is also always ready for those outcomes.
A good social engineer is always planning an attack, and, just like in chess, they are typically several moves ahead of the victim. The most common technique involves gaining the victim’s trust, something that a social engineer is quite good at. It is human nature to have a built-in sense of security and the belief that it is highly unlikely that someone is looking to deceive us. When were were children, we were taught to never open doors to strangers. Perhaps we should also stick to that old rule in today’s faceless and voiceless digital world.
Gray number area
It is worth mentioning that no security report provides us with the true picture or the real number of incidents in a certain time period. There are several reasons for that but the most common one is that security incidents go unreported to avoid financial consequences, such as losing markets over a poor public image, or simply to cover up incidents to make the outward image better than it really is. Source: https://www.enisa.europa.eu/topics/cyber-threats/threats-and-trends.
In the report, prime threats identified include:
- Ransomware
- Malware
- Social Engineering threats
- Threats against data
- Threats against availability: Denial of Service
- Threats against availability: Internet threats
- Disinformation – misinformation
- Supply-chain attacks
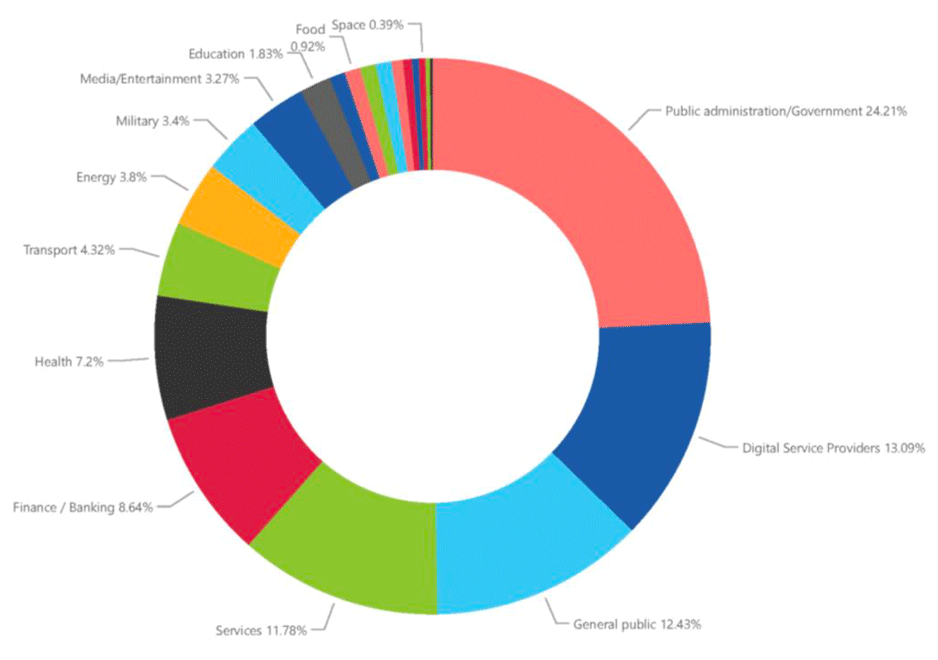
When the report is read carefully, it is worth noting that the most common initialization vector of attack is a social engineering.
These attacks are mostly focused on public institutions and digital service providers. This is to be expected as digital service providers provide public institutions with new software solutions. Interestingly enough, the general population is ranked third on this list. This means that it is only a matter of time before we all become victims of some type of cyberattack.
The most popular technique
Social engineering, phishing in particular, is a popular technique used by attackers for malicious activities. According to the Verizon Data Breach Investigations Report (DBIR, source: https://www.verizon.com/business/resources/reports/dbir/), approximately 82 percent of all analyzed breaches in Europe involved a human element, while around 60 percent of breaches involved one of the components of social engineering. The reason for that is quite simple. Email is the easiest medium for malicious attackers to get to their potential target; besides paying for your internet subscription, sending emails costs you absolutely nothing. Moreover, Verizon DBIR shows that attackers continue to use stolen passwords to gain more information about their target by using the company email.
The end goal of using information gathered from a company account is creating real scenarios and even more sophisticated attacks on companies, such as business email compromises (BECs). Financially speaking, a BEC is one of the most devastating forms of cybercrime. It is so devastating because, besides not having to take on the challenges of a multistage form of attack and finding their way in a company’s unknown environment, the attackers can simply request an execution of, for instance, a financial transaction via an email from a high-ranking executive whose email address had been gathered during the first stage of the phishing campaign.
The threats that could harm our privacy or the company’s information systems might not seem real until they are carried out. But the reality is, it’s only a matter of time before they do happen. To avoid such a costly reality, we all need to become aware of the danger, stay alert, and aggressively protect our information assets and personal data. And we need to implement these precautionary measures today.
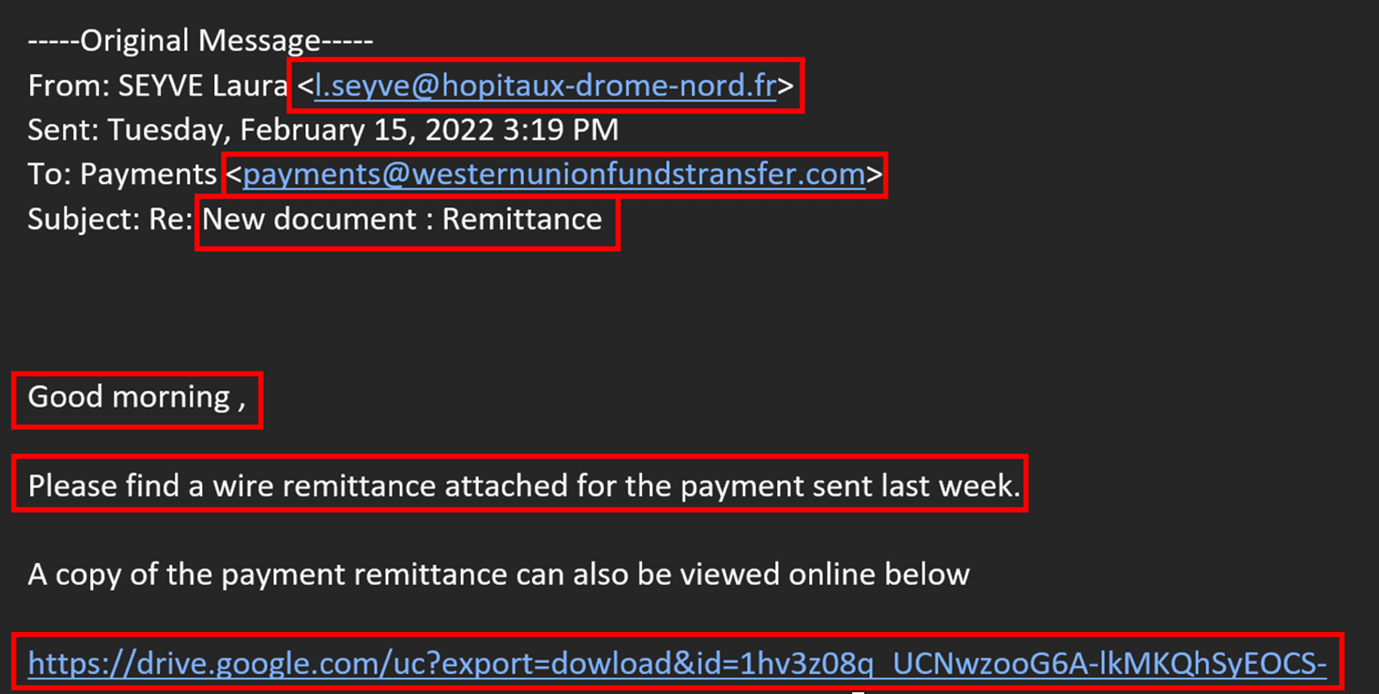
Example
In the example above we can see the most common type of phishing email received by our company. In the red boxes are red flags that you should look out for in order to identify phishing emails. The First sender’s e-mail address looks very suspicious. The domain looks legitimate, but if we google the “hopitaux drome nord” we stumble upon some hospital in France. The first question in your mind has to be, did we have anything to do with that entity? Secondly, “westernunionfundstransfer” is listed as the domain to which the email was supposedly sent. Always double-check the domains of money transfer services. They often look pretty similar, but they usually are only one or two characters “off”, or the domain is different to what it should be. Next, although phishing campaigns now are more sophisticated than ever, sometimes typfellers occur. In the case above after “Good morning” there is a space, then a comma. Last, but not least, look at the hyperlinks in the emails. As aforementioned, phishing campaigns are getting sophisticated, and links are masked under some “legitimate” buttons, so always double-check hyperlinks and find out where they are directing to. Here is an example of a Google Drive link. Never, never, click on links pointing to Google Drive, Dropbox etc. If hyperlinks are masked under the buttons in the email, move the cursor to the button and hover, and wait for a second or two. In the bottom left corner you will see the actual hyperlink where that button directs to. If it is slightly off or you are not sure, it is better to contact your IT department rather than checking where it actually goes. One piece of advice, an internet site called Virustotal (https://www.virustotal.com/) is a great place to start investigating any suspicious domain, URL, file, etc. It is a free website that inspects items with over 70 antivirus scanners and URL/domain blocklisting services.
Education and education alone
To reduce the attack surface area to a minimum, it is necessary to emphasize the importance of education – in this case, education for all, from secretaries, administrative and financial staff, all the way up to company leaders. I would even say that they all should undergo special training as they belong to the category of people who are most often targeted by the attackers because they have access to the most sensitive information used in these attacks. It is vital to understand that the bosses are not the only ones with access to information that an attacker can use.
These days, staff across all levels and with different authorization can be targeted by attackers. We should also highlight periodic training; data has shown that when we learn new information, it tends to fade away over a period of time. Also, with time, users tend to start paying less attention to the security elements highlighted in their training. That is why repetition is the mother of learning.
Furthermore, a corporate security policy must clearly define both acceptable and unacceptable behavior in the workplace. What does that mean? If, at your company, phone numbers are used for identification, then those numbers must be treated as sensitive information, not to be shared with everyone but carefully guarded. This goes for any other form of identification, including email addresses, not to mention passwords.
My precious password
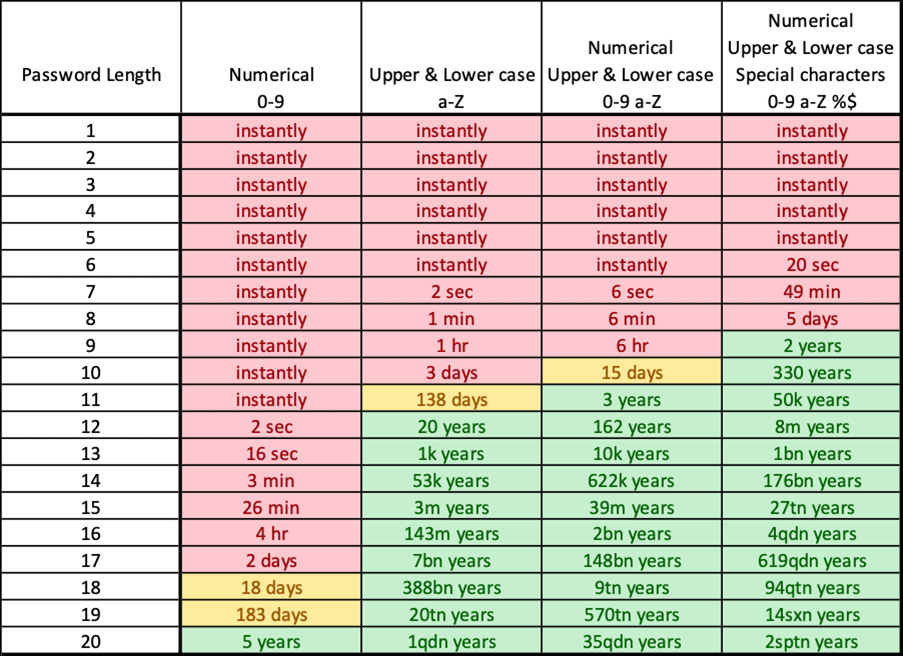
Ah, those passwords, who can remember them all? With hardware power increasing year after year, although no longer according to Moore’s law, cracking passwords with brute force (a method that involves repeated login attempts using every possible letter, number, and special character combination to guess a password) is surprisingly quick. To manage your passwords, you should use one of the available tools for storing them, such as, for instance, Bitwarden (https://bitwarden.com); it works on both web browsers and mobile phones, and everything is linked to a single user account. You will still have to remember one password but now you will be much safer.
But how can you have a secure password that is long and easily remembered, but also meets the complexity requirements? Start by picking a phrase, a favorite verse, or a quote that only you would remember. Do not use names of your close family members or pets.
Here’s an example: Noc1je2pun@Zvij3zda! This particular verse has numbers ‘1’ and ‘2’ instead of the first two blank spaces, special character ‘@‘ instead of the letter ‘a’, number ‘3’ instead of the letter ‘e’, and an exclamation mark at the end. Or how about 0tisao1sam2na#TrgPtica, or The-Phantom-Of-The-Oper@? You get the idea, right? Excellent, just don’t go using these examples now.
Summary
Your business cannot afford to let down its guard and become vulnerable for a single second. Don’t rely on network protections or firewalls to protect your information. Stay focused on the weakest link in your chain, which is typically people.