Veronika Vrhovec
DATA ENGINEER
Let’s Demystify Data Security
To implement data security principles in our businesses and habits, we need to understand the concept of it, and know which methods we have at our disposal to prevent the data breach.
Data security is a subfield of cyber security that studies and implements sets of methods and processes, that protect digital data from corruption, confidential information from unauthorised access, and prevent system breaches.
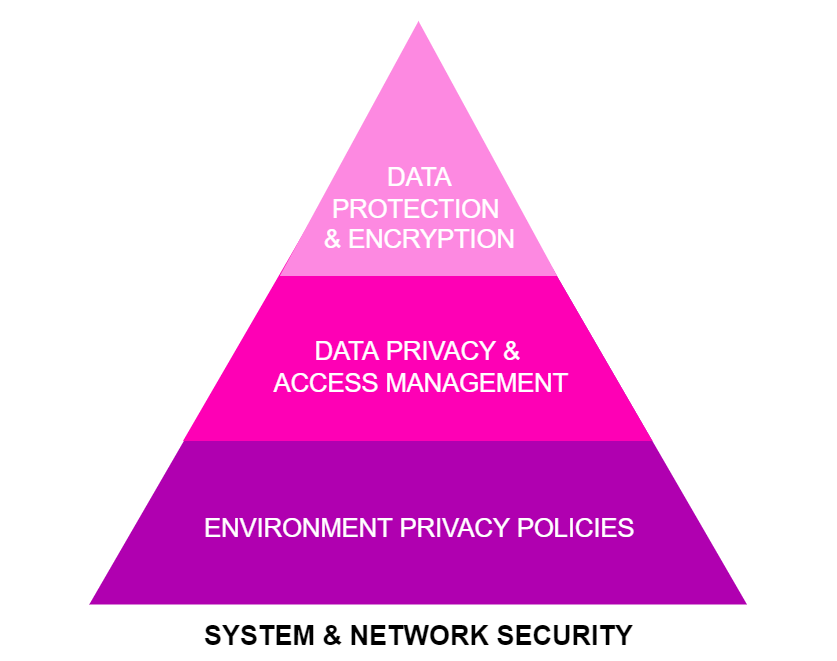
Some means of implementing security to the system include designing the data encryption procedures, defining data privacy policies throughout the environment, and establishing data protection methods, as is represented in Figure 1.
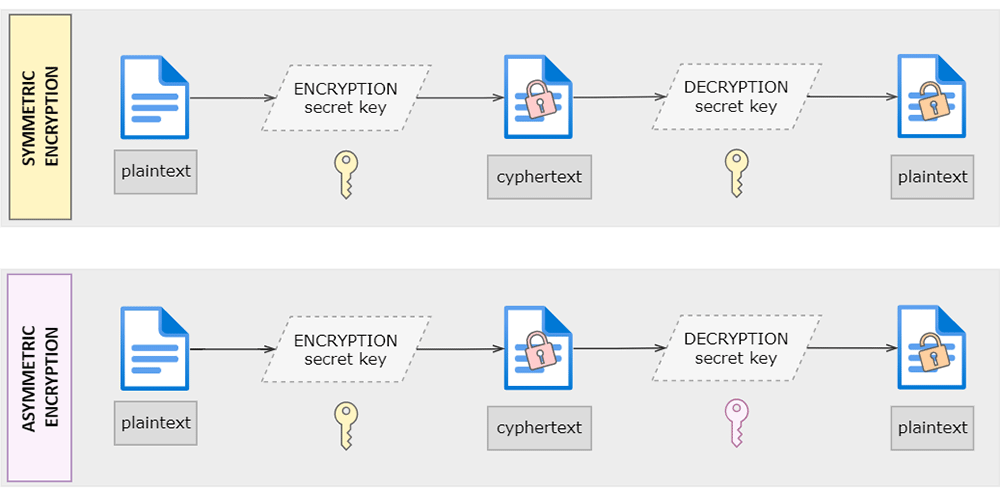
These processes will all be covered in the following articles in much more detail, but it’s never too soon to start thinking about them. The first step in establishing a secure environment for the data we process, is to analyse the system that is in use so the appropriate procedures can be imposed on it. Start low and grow high. This analysis should indicate how vulnerable the system is, so the actions of securing it can be prioritised. Even though writing a solution specific to our needs is tempting, it might be a smarter choice to use some of the existing services or applications that are being kept up to date and in accordance with Regulatory Compliance. All the servers and personal computers that use the internet to transfer the data should be using a Virtual Private Network (VPN) service. A VPN provides a secure, encrypted connection from the user’s computer to the public internet by providing a private tunnel that secures the data traffic and keeps the user’s operations on the internet private. While it protects the data being transferred over the internet, it doesn’t secure the data trafficking over the business network. To ensure the Wi-Fi network, Wi-Fi Protected Access 3 (WPA3) encryption should be established. Other good practices include keeping the firmware updated, setting up two-factor authentication (2FA) for logins to services, enabling encryption functions for the network, encouraging users to use password managers, and configuring the access management based on the principle of least privilege. There already are good encrypting algorithms that can easily be put into action and adjusted to suit specific needs, so that even if the data is intercepted, it can’t be decrypted without the private key. There are two main types of encryption. Symmetric encryption that uses the same private key for both encrypting and decrypting, and asymmetric encryption that uses one private key for encrypting, and another one for decrypting, as shown in Figure 2.
Now that we have briefly introduced the processes, here comes the hard part – changing the way we work and do things. Having them defined, and not implemented doesn’t do a thing to establish data security. People are dependent on habits and routines, and some RESEARCHERS say that it takes us approximately 21 days to form a new habit and 90 days to make it part of our routine. The numbers are not set in stone, but the idea of needing the adjustment time for new habits to grow into our behaviour stands. Therefore, it’s important to explain the need of incorporating new security procedures to the users so that they will accept them and confidently use them, with them eventually becoming just another part of everyday life. This can be achieved by defining the security policies for the company and putting them into practice. Some of the policies include setting up the principle of least privilege for the processes that different user roles work with, defining backup policies, and data loss prevention (DLP) procedures for data archival.
A RECENT report says that due to an error in the backup system of a university’s supercomputer, 77 TB of research data is forever lost.
So, does establishing all those Security Procedures really pay off?
Most people still haven’t made it a priority to secure their personal digital fingerprint. Some of the most common explanations they offer is having nothing to hide, or not being interesting enough to have their personal information stolen. On the other hand, the business world slowly became aware of the importance of operating securely. The data processed by companies can be put into two categories. One covers the log files and metadata, and the other is confidential information such as business data, user and customer personally identifiable information (PII data) and financial data.
Confidential data is non-public personal or business data that, upon illegal access, causes public identification of a person or a business case.
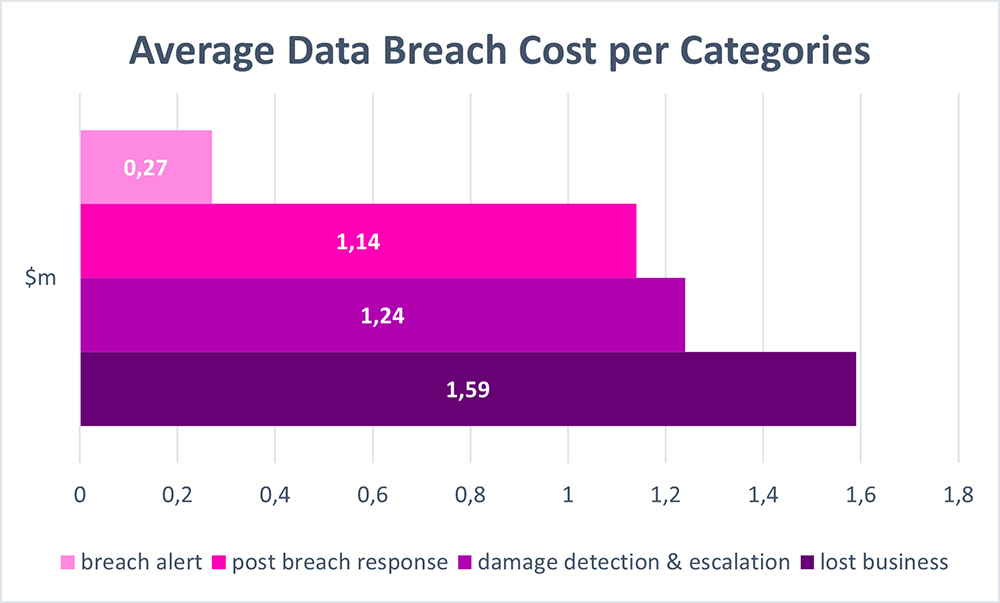
Leaking confidential information can not only cause companies to lose their status or competitive advantage, but also could mean that they face charges of breaking the privacy laws such as GDPR, HIPPA, PIPEDA, CCPA, APP, CSP234 and others. RESEARCH covering the data breaches that occurred in 2021 shows that an average data breach costs a company around $4.24m. The chart in Figure 3. displays the cost distribution per components.
We can see that damage control is what costs the companies most – losing the client’s trust, suffering lawsuits for breaking the confidentiality agreements, and responding with immediate actions to regain the systems’ security. The same research also indicates that 44% of all attacks were aimed at the PII data, costing around $180 per record. Imagine what would be the minimal cost of a cyberattack aimed at the user database for an active social network?!
RESEARCH from 2016 reports a breach into a user database system exposing 360 million credentials, with SELLING PRICE of 3200$ per record.
Remote work is another aggravating factor in securing the system and data because it merely relies on users’ personal networking infrastructure. With the rising trend of remote and hybrid ways of working, it becomes harder to secure business operations, so it is no surprise that the numbers of hacking attacks have a rising trend in the last couple of years.
A data breach into a remote work environment costs on average $1,07m more than the same kind of breach into the office environment, ANALYSIS shows.
Last year remained challenging when it comes to handling business in the times of global uncertainty (and with current happenings in 2022 we are yet to see if they took a turn for the worse). Some companies survived without suffering any hacking attacks, some were targeted often which caused a huge impact on their financials, and most of the world fits somewhere in between. Companies usually have some assurance policies in case of a data breach or hacking attack, so the costs for that are mostly pre-calculated into their budget. It is, therefore, more important to get the knowledge from these incidents to know how to prevent them from happening again. Data security surely is in the category of things that is better to be considered before an incident, rather than after. In conclusion, be responsible when dealing with actions that include sensitive data, especially if you are trusted with someone else’s PII or business data. Analyse the security of the system in use, and incorporate strong security policies, so that everyone involved can sleep peacefully.